The hidden cost of blocking — why your AdBlock slows you down and compromises your anonymity

Introduction
In the pursuit of efficiency and traffic savings, installing an ad blocker seems like an obvious step. But what if this familiar optimization tool is actually a hidden threat that compromises your digital fingerprint?
In this article, we will analyze the fundamental vulnerabilities of standard blocking methods and present a fundamentally different approach, designed specifically for multi-accounting tasks. For those who value practice over theory, we suggest you jump straight to the results of our comparative testing.
Why Popular Blockers are a Dead End for Anti-Detect Browsers
Two dominant approaches have emerged in the market: browser extensions and DNS filtering. Both, at first glance, solve the problem. But for the world of anti-detect browsers, where the anonymity and reputation of a profile are at stake, these solutions prove to be not just ineffective, but downright dangerous. Let's break down why.
Compromise #1: Browser Extensions — Slow and Detectable
The most obvious path is to install a familiar extension like AdBlock Plus or uBlock Origin. It operates within the browser's "sandbox" and, seemingly, does its job. But in practice, this creates three critical vulnerabilities.
First, it's a performance trap. It's important to understand that while extensions can block network requests before they are sent, the key problem lies in the cost of this operation. All filtering logic is executed in a JavaScript environment, creating a significant additional load on the processor and RAM. This problem doesn't just exist; it scales linearly and is detrimental to your work: if one profile with a blocker consumes an extra 100 MB of RAM, then 50 simultaneously running profiles will require an additional 5 GB of RAM just to service the extensions themselves. As a result, the benefit of blocking is partially eaten up by delays and the resources spent on the "filter" itself.
Second, it's a betrayal of anonymity. Any third-party extension is an additional and very noticeable variable in your digital fingerprint. Advanced anti-bot systems have direct access to the list of installed extensions and their behavior. This is not a theoretical risk, but a practical vulnerability that is easy to verify.
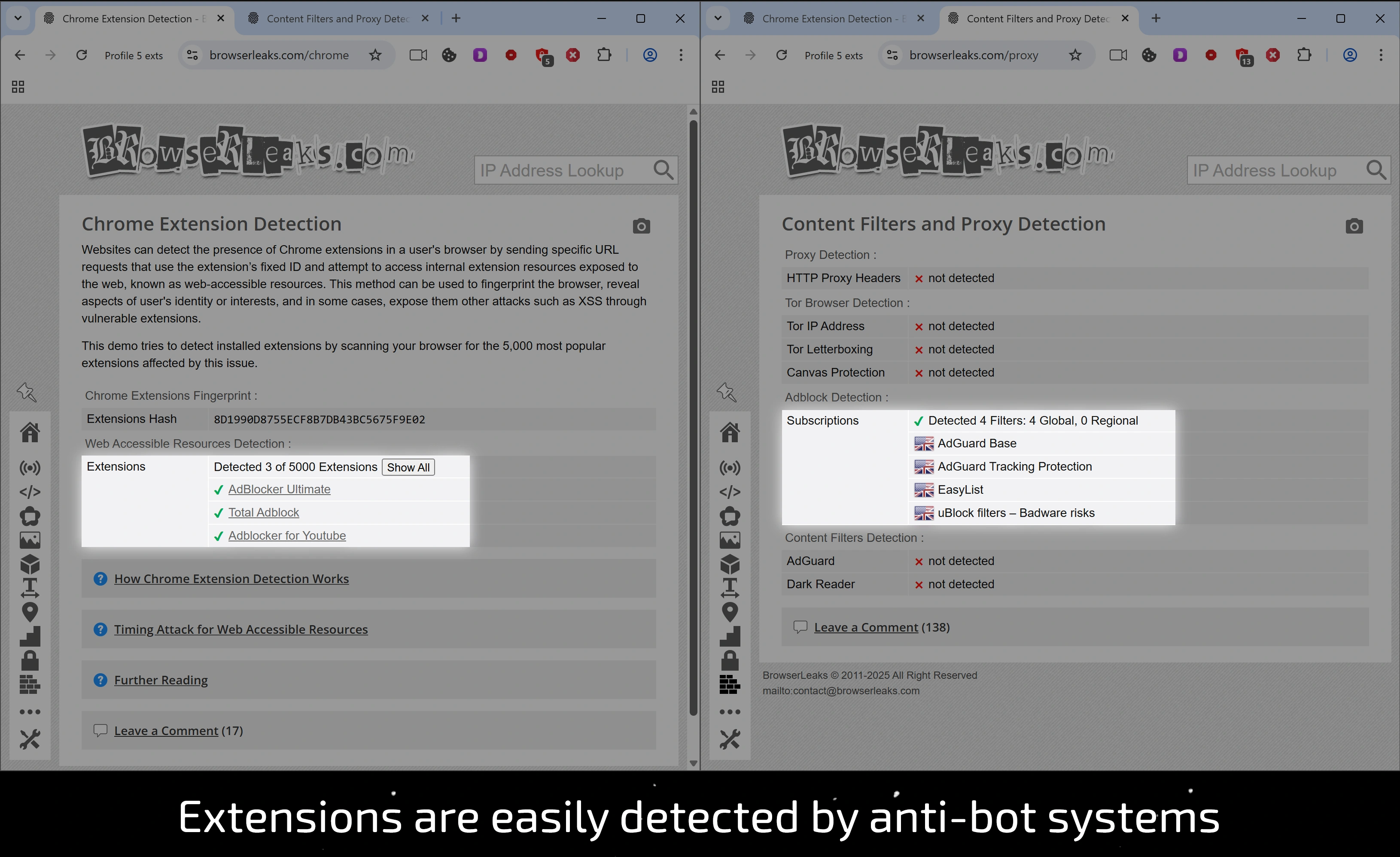
Detecting the presence of such an "assistant" is a trivial task that immediately flags your profile as suspicious. You are trying to blend in with the crowd, but at the same time, you are wearing a bright, flashing badge that says "I use AdBlock."
And third, it's a technological dead end called Manifest V3. Google, the developer of the Chromium engine on which most anti-detect browsers are built, has dealt a serious blow to the effectiveness of blockers. With the transition to Manifest V3, extensions were deprived of their main tool — the powerful webRequest API, which allowed for flexible analysis and blocking of traffic "on the fly."
Instead, they were offered a limited declarativeNetRequest, which requires providing the browser with a static list of rules in advance, with a strict limit — no more than 30,000 entries.
To understand the scale of the problem, just look at the size of popular filter lists:
- EasyList (the basic list for most blockers): ~70,000 rules
- AdBlock Plus (with additional lists): ~100,000+ rules
- uBlock Origin (in full configuration): up to 2,000,000 rules
This means that even basic filters exceed the Manifest V3 limits by 2-3 times, and advanced ones by up to 67 times. Extension developers are forced to either cut functionality, throwing out tens of thousands of rules, or use inefficient workarounds. In any case, the user gets only a shadow of the former protection, which fatally reduces the quality of blocking in modern browser versions.
Compromise #2: DNS Filtering — A Crude and Blind Tool
Alright, if extensions aren't suitable, maybe we should go a level lower — to the network level? DNS filtering blocks access to entire domains known for advertising or tracking. It sounds reliable, but in reality, it's an even cruder and more imperfect method.
Its main drawback is the lack of cosmetic filtering. A DNS server will successfully block a request to the ads.google.com domain, but it has no idea how this will affect the page. As a result, you get sites riddled with "holes" — empty frames, blocks with loading errors, and a broken layout. This solves the traffic problem but kills the user experience.
Furthermore, a DNS filter is completely blind to "internal" advertising. It is powerless against sponsored posts in a Facebook feed, promotional products in an Amazon search, or pre-rolls on YouTube, because all this content is loaded from the same domains as the main content. Attempting to block them at the DNS level will lead to the entire site being blocked.
Finally, DNS filtering is easily detectable. An anti-bot system can initiate a test request from the browser to a known advertising domain from public blacklists. If the request fails and is blocked, remaining visible at the browser level, the system determines with high accuracy that content filtering is being used. This is a simple and effective test that nullifies your masking efforts.
As we can see, the market offers two compromised paths: either a slow, noticeable, and technologically outdated solution in the form of extensions, or a crude and blind intervention at the DNS level. Neither option meets the high demands for speed, anonymity, and efficiency that professionals require.
This led us to ask a different question: what if the problem is not with the filter itself, but with the architecture of its application? What if we stop fighting the consequences at the application or network level and eliminate the root cause at the browser architecture level?
AdCrusher — The World's First Blocker Integration at the Core Level of an Anti-Detect Browser
Faced with the fundamental compromises of existing approaches, we realized that the solution to the problem does not lie in add-ons or external services. It became clear that any external traffic control is by definition slower and less reliable than a native, proactive mechanism. The only way to achieve absolute control, speed, and stealth is to build the filtering mechanism into the very component that generates network requests.
We didn't fight the consequences; we eliminated the root cause by integrating the protection mechanism directly into the browser's architecture.
Introducing AdCrusher — the first content filtering technology in the anti-detect browser market implemented directly at the core level of Chromium. It is not an extension and not a DNS filter. It is a native, high-performance component written in Rust and integrated into the browser's "engine." It sees and controls every network request even before it is sent.
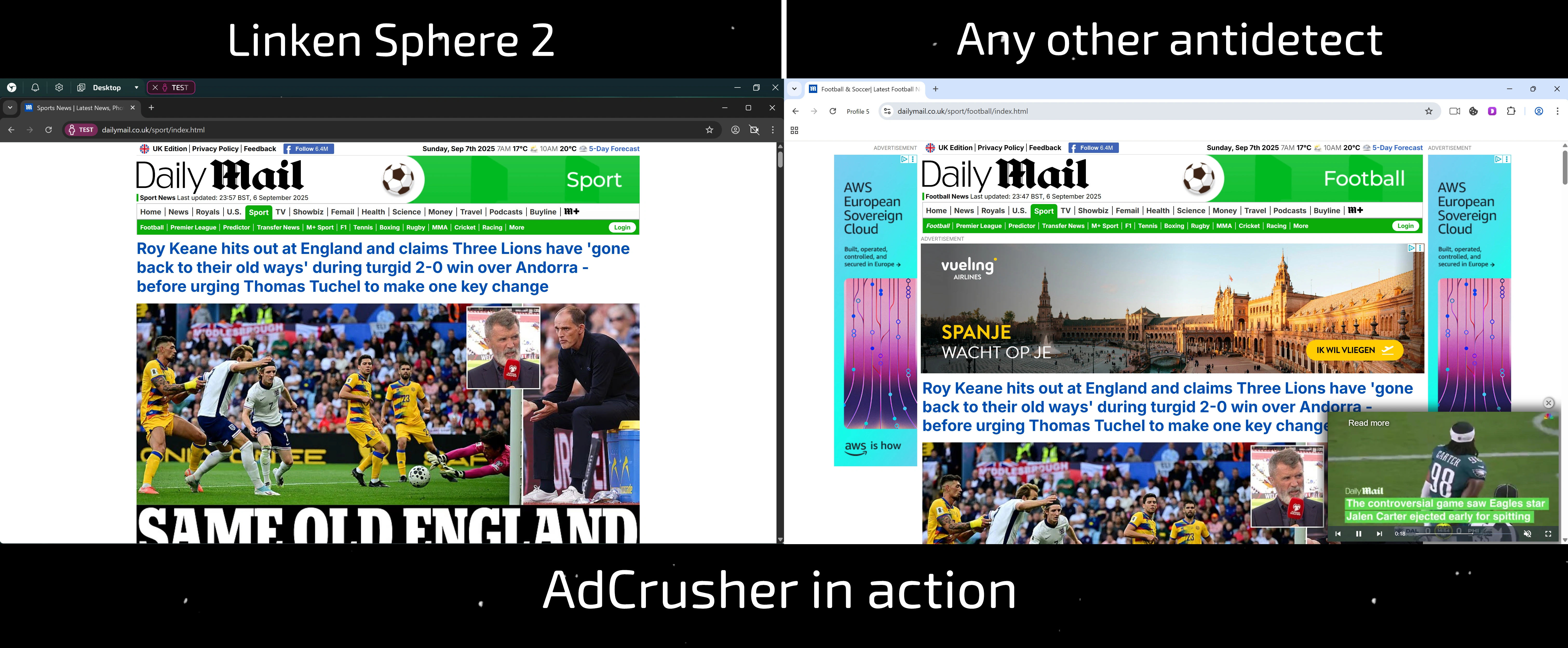
How does it work?
Our technology is a multi-level protection system where each component solves its own task, creating a comprehensive and seamless barrier for unwanted content.
1. Blocking Network Requests
This is the foundation of our system. Unlike extensions, which operate as a separate software layer, AdCrusher analyzes a network request at the initiation stage. If the target is a known ad server, tracker, or analytics system, the request simply never leaves the browser. It is blocked at the earliest stage, which ensures maximum traffic savings and zero load on the network.
2. Intelligent Cosmetic Filtering
We understand that blocking ads is half the battle. The other half is making the page look perfect. Our cosmetic filtering module analyzes the HTML structure and carefully "cleans up" all traces of blocked elements, preserving the integrity and aesthetics of the layout.
3. Resource Replacement and Iframe Protection
The technology can not only block but also replace resources "on the fly," neutralizing malicious or resource-intensive scripts without compromising site functionality. A separate module controls the creation of iframe elements, which are one of the most popular containers for intrusive advertising, preventing their appearance.
What does this mean for you in practice?
Technical superiority is meaningless if it doesn't solve real user problems. Here are three key advantages you get "out of the box":
Workflow Transformation Through Speed
By eliminating hundreds of unnecessary requests and scripts, the loading speed and responsiveness of pages increase significantly. For those who work with dozens and hundreds of profiles, this means hours of saved time every day and a fundamentally new level of comfort and productivity.
Direct Financial Savings
For everyone who uses proxies with pay-per-traffic billing, AdCrusher becomes a powerful tool for cost optimization. By cutting off up to 40% of "junk" traffic, the technology directly reduces your proxy bills, paying for the subscription many times over and turning AdCrusher from a feature into your financial instrument.
Absolute Stealth
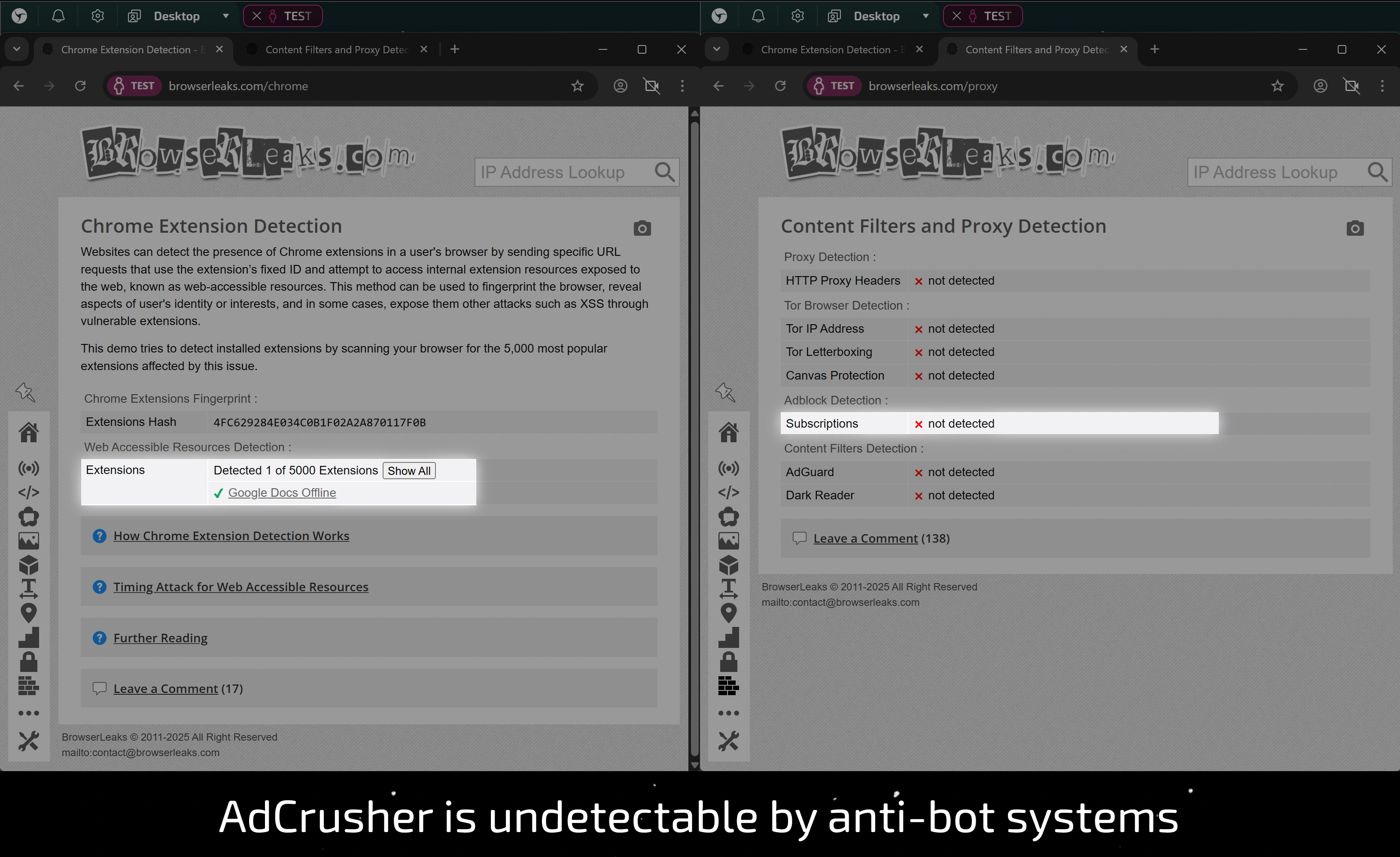
Since our technology is a native part of the browser, it leaves no traces in the digital fingerprint. Websites and anti-bot systems cannot detect it, unlike extensions or DNS request anomalies. This provides an additional, previously unattainable level of masking and security.
And all this starts working after checking a single box in the session settings. No complex configurations or installation of third-party components.
AdCrusher sets a new standard for performance and security for professional work.
How to activate AdCrusher in Linken Sphere?
To activate the built-in ad and tracker blocker AdCrusher, you just need to follow a few simple steps. The entire process is clearly demonstrated in the video instructions above.
- Open the session settings: to do this, click on the three-dot icon on the right and select "Edit" from the drop-down menu.
- Enable AdCrusher: in the settings window that opens, go to the "Misc" section and check the box next to the "AdCrusher" option.
- Save the changes: click the "Save" button at the bottom of the window.
Done! AdCrusher will now be active for the selected session.
It is worth noting that this option can be enabled not only for existing sessions. You can activate it when creating a new session or even add it to a settings preset — in this case, all new profiles created based on it will be protected from ads and trackers by default.
Comparative Testing: The Real Cost of Traffic
To clearly demonstrate the economic advantage of AdCrusher technology, we conducted a direct comparison of Linken Sphere with four popular anti-detect browsers on the market. Our goal was to measure one of the most critical parameters for our users — actual traffic consumption when working with a popular website.
Testing Methodology
To create equal and absolutely reproducible conditions for all participants, we used the Charles debugging proxy. With its help, we artificially limited (throttled) the connection speed to the level of a typical 4G network. This allowed us to minimize the influence of internet speed fluctuations on the purity of the experiment and ensure that all browsers were in identical conditions.
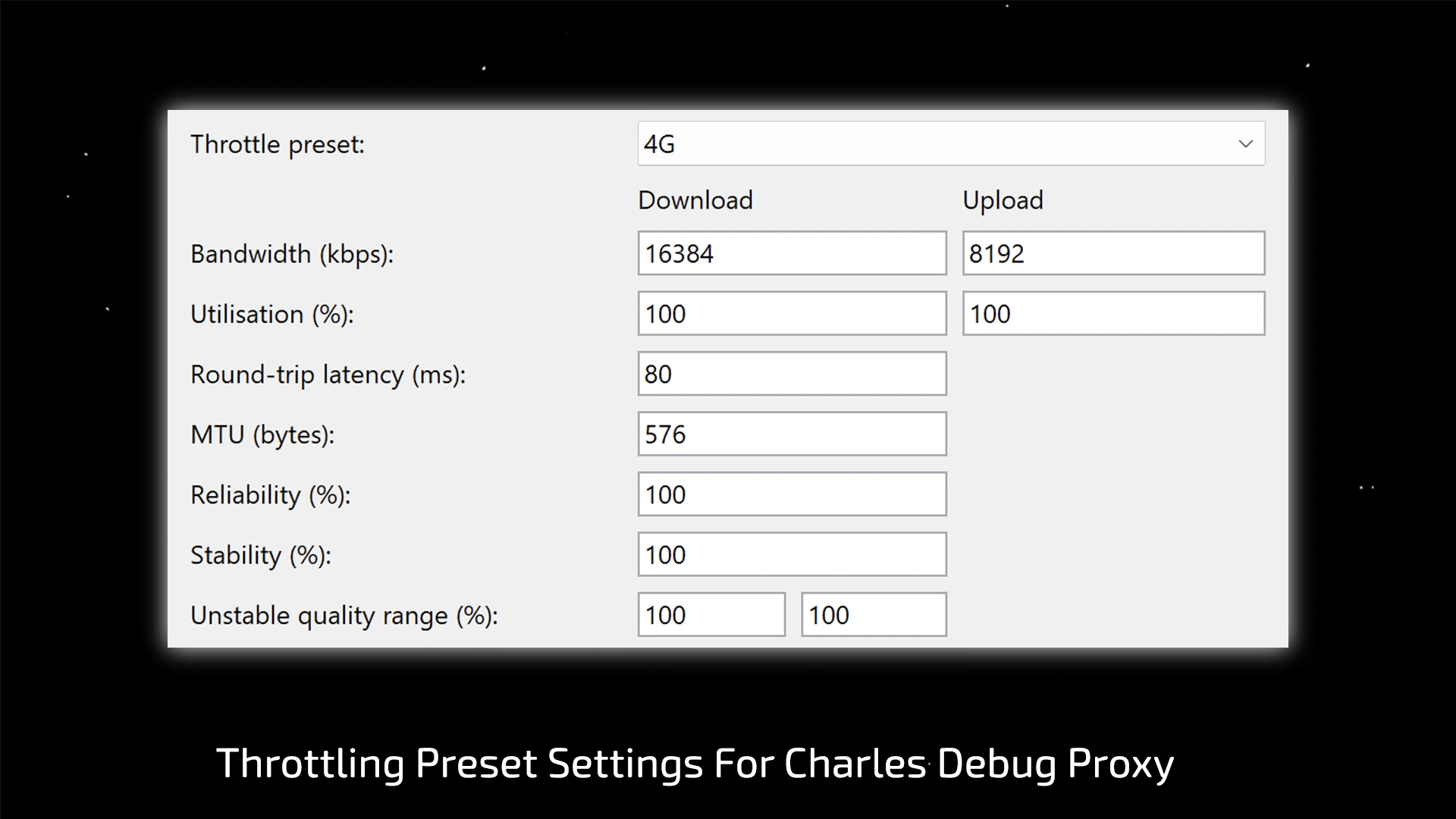
On each of the five browsers, we measured the amount of traffic required to fully load the amazon.com homepage. For each browser, five independent measurements were taken (each time on a new, clean profile without cache), after which we calculated the arithmetic mean.
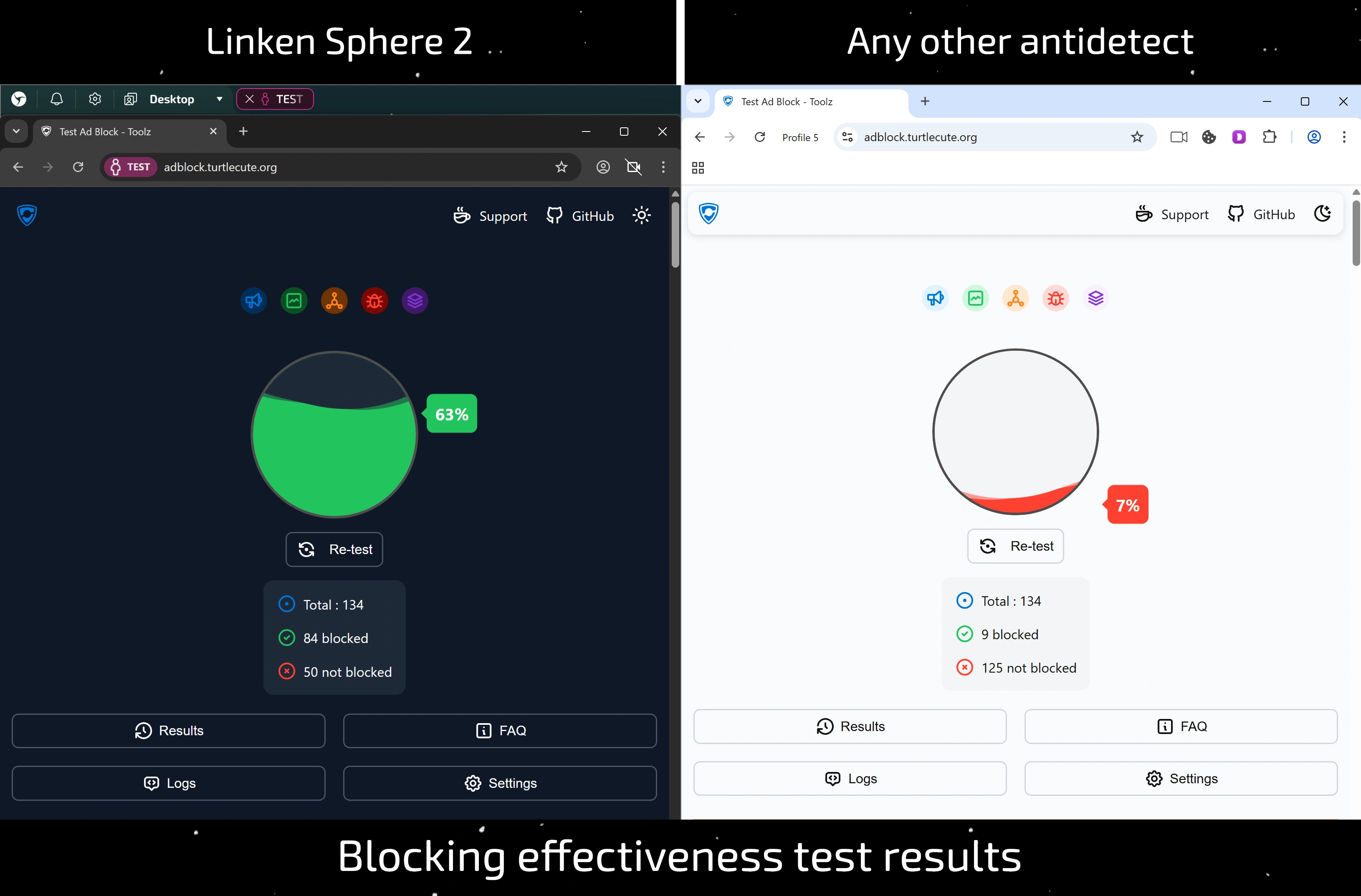
Results
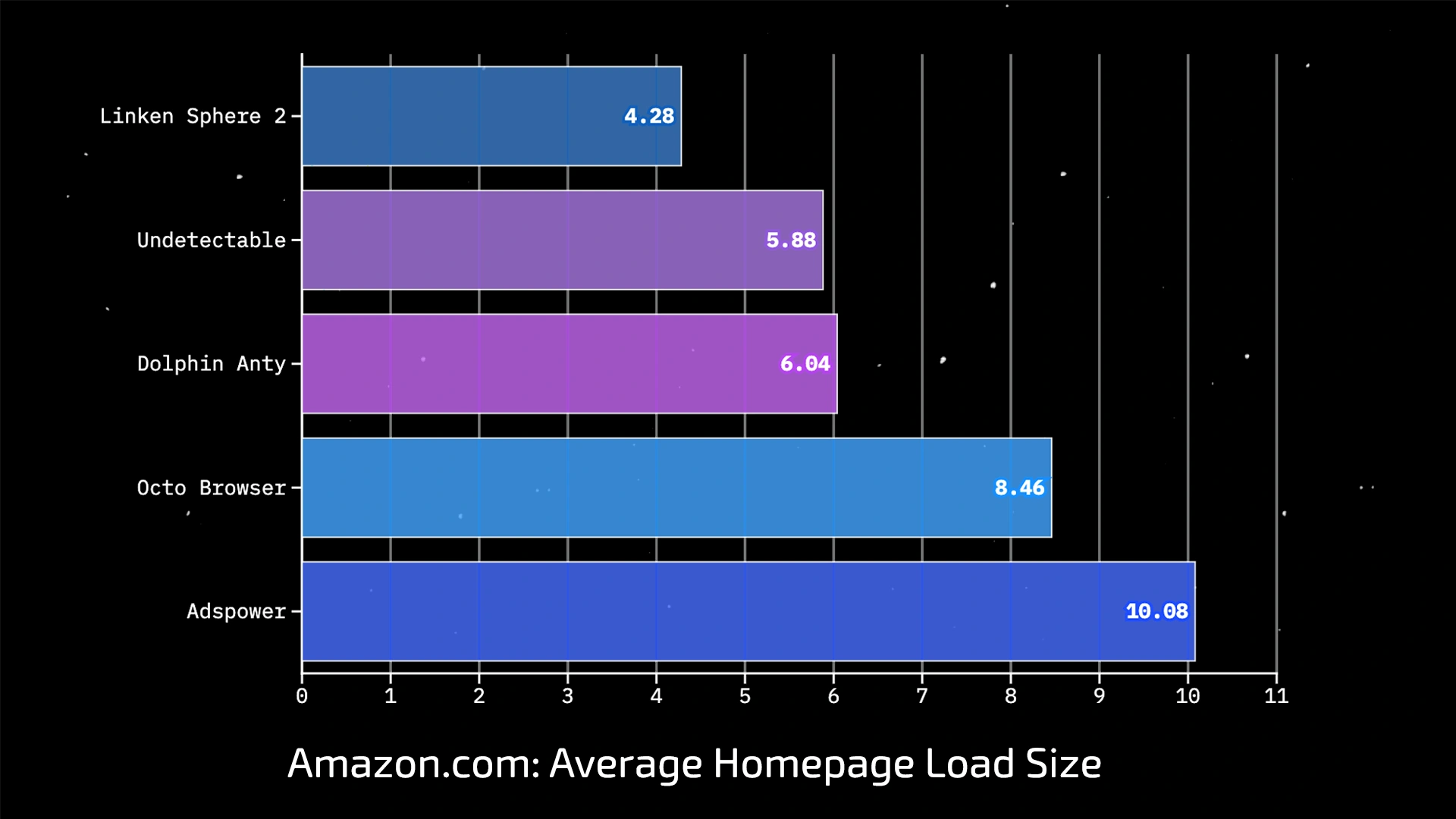
What do these numbers mean for you?
Linken Sphere with AdCrusher technology showed a result of 4.28 MB. This is:
- 2.35 times less than Adspower (10.08 MB).
- Almost half as much as Octo Browser (8.46 MB).
- 37% more efficient than the closest competitor, Undetectable (5.88 MB).
What is the reason for such a significant difference? It's simple. While Linken Sphere cuts off dozens of heavy advertising scripts, trackers, and unnecessary elements at the core level before they are even loaded, other browsers are forced to download all this "digital junk." Extra data that you ultimately pay for.
Let's translate this into money. The difference with Undetectable is 1.6 MB on a single page load. If you load 500 similar pages a day (a completely standard workload), that's already 800 MB of saved traffic. On a monthly scale, that's 24 GB. At an average price of $4 per gigabyte for mobile proxies, AdCrusher saves you $96 per month compared to even the most efficient of its competitors. And compared to Adspower, this saving will exceed $270.
Thus, effective blocking at the core level is not just a convenient feature for comfortable work. It is a direct and measurable economic advantage that allows you to both reduce costs and get significantly more traffic within the same budget.
Conclusion
For a long time, the multi-accounting market offered users only a forced compromise. One had to choose between slow but functional extensions that jeopardized anonymity, and fast but crude DNS filters that broke layouts and were powerless against built-in advertising. You sacrificed either speed, or stealth, or convenience.
AdCrusher is not just another improvement, but a fundamental architectural shift. By integrating filtering technology directly into the browser core, we have eliminated the cause of the problem itself, not its symptoms. This has allowed us to achieve a triple effect: a radical acceleration of work processes, absolute stealth from anti-bot systems, and, most importantly, direct and measurable financial savings.
We urge you to view AdCrusher not as a new feature, but as a rational business decision. Update Linken Sphere to the latest version, activate AdCrusher in the session settings, and see for yourself how your traffic consumption decreases. Stop paying for excess traffic that slows down your work and eats up your proxy budget. In a world where every second and every megabyte directly affects profit, effective filtering becomes not a luxury, but an economic necessity.

